In today’s interconnected world, the importance of safeguarding sensitive information cannot be overstated. With the ever-increasing volume of data being generated and collected, the need for robust data security measures is paramount. In this blog post, we will delve into the intricate co-relation between data privacy and information security. We will explain their significance and explore how they collaborate to protect sensitive data.
Understanding Data Privacy and Information Security- The Co-Relation
Data privacy and information security are often used interchangeably, but they have distinct roles in the protection of data. Data privacy primarily focuses on safeguarding Personally Identifiable Information (PII) – those critical data points that can identify individuals. On the other hand, information security is a broader concept. It encompasses not only PII but also the protection of all confidential information within an organization.

Data Privacy: Consider a company that collects personal information from its customers. To maintain data privacy, it must have a privacy policy that outlines how the data will be used, who will have access to it, and how it will be protected. The company must also obtain consent from its customers before collecting their personal information. This ensures that the company respects individuals’ privacy and complies with relevant regulations.
Information Security: Imagine a company that stores sensitive data on its servers. To ensure information security, it should implement measures like firewalls, encryption, and access controls. These measures help prevent unauthorized access. Additionally, the company must have a data backup and recovery plan in case of a security breach. This demonstrates the organization’s commitment to safeguarding all its confidential information.
To mitigate risks effectively, companies and individuals must implement best practices for both data privacy and information security. This is to protect their data and maintain the trust of their customers.
CIA Triad – Confidentiality, Integrity, and Availability
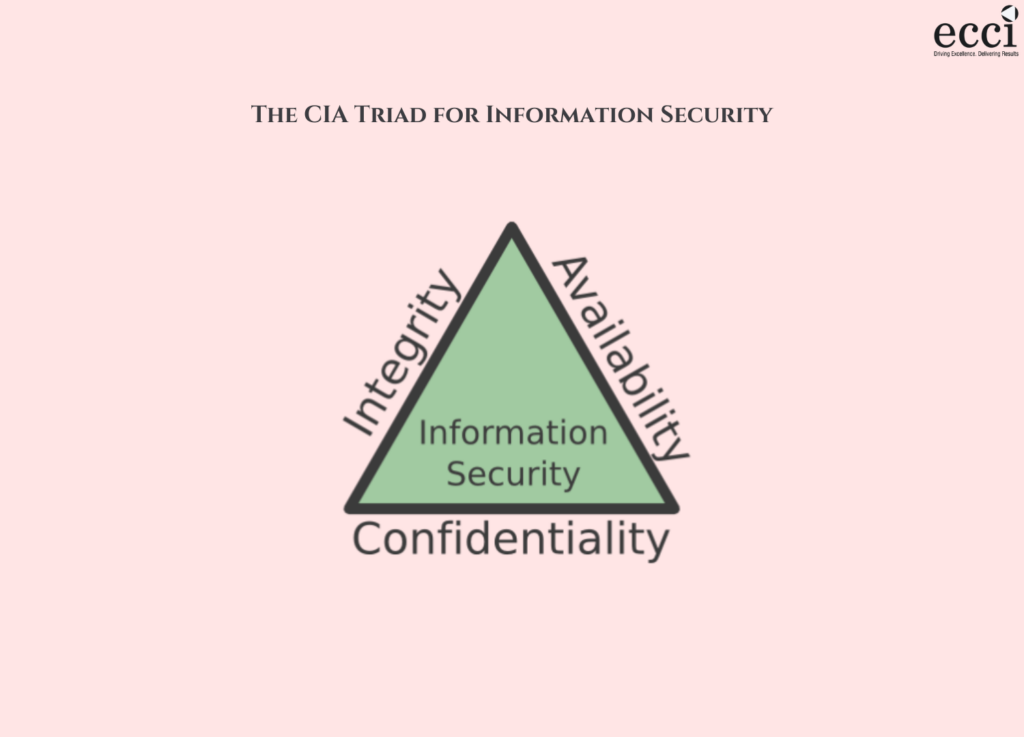
To understand the core principles of data privacy and information security, we must acquaint ourselves with the CIA Triad. This fundamental security model consists of three key elements:
1. Confidentiality: Ensuring that data is accessed only by authorized users with the proper credentials.
2. Integrity: Maintaining the reliability and accuracy of data while protecting it from unwarranted changes.
3. Availability: Ensuring that data is readily accessible for ongoing business needs while remaining secure.
Best Practices for Data Privacy and Information Security
To protect data effectively, it is essential to adhere to best practices. These practices form the bedrock of a robust data security strategy. Let’s take a closer look at some of them:
For Data Privacy:
Perform Data Discovery: Start by discovering what data exists, determining its sensitivity, and ensuring compliance with security regulations.
Control Access to Sensitive Data: Limit access to sensitive corporate data to individuals who genuinely need it.
Use the Principle of Least Privilege (PoLP): Ensure that access to sensitive data is granted based on necessity, reducing the risk of insider threats.
Encrypt Your Data: Data encryption converts information into an unreadable format, making it challenging for unauthorized users to access.
For Information Security:
Install Anti-Malware Software: Protect your devices from malware, which can compromise confidential data.
Perform Vulnerability Assessments and Audits: Regular assessments ensure that your system is up to date, secure, and less prone to data breaches.
Create and Implement Employee Security Training: Educate employees on data security to mitigate potential threats and enhance overall awareness.
Physically Safeguard Data: Not all data is digital; some are still stored in physical formats, requiring physical security measures.
How Data Breaches Occur When Data Privacy or Information Security Is Compromised?
Data breaches represent a significant and growing threat to the security of personal and sensitive information in today’s digital age. They occur when data privacy or information security measures are compromised, leading to unauthorized access or exposure of confidential data. Understanding the mechanisms behind data breaches is essential for individuals, organizations, and policymakers to implement effective preventive measures and response strategies.
1. Inadequate User Access Control: Failing to control access to sensitive data can lead to unauthorized personnel accessing confidential information.
2. Unencrypted Data: Neglecting to encrypt data can expose it to breaches if cybercriminals gain access.
3. Insider Threats: Employees with excessive privileges can misuse sensitive data for malicious purposes, highlighting the need for the Principle of Least Privilege.
4. Lack of Regular Training: When employees are not adequately trained, they may inadvertently compromise data security.
When data privacy or information security is compromised, it can lead to devastating data breaches. These breaches can occur in various ways, highlighting the need for a cohesive strategy that bridges the gap between data privacy and information security. Let’s explore the co-relation further:
5 Cases of Data Privacy Violations in the Philippines
To underscore the real-world consequences of data privacy violations, here are five cases from the Philippines where data breaches have occurred, compromising the personal information of individuals. These cases serve as stark reminders of the importance of maintaining stringent data privacy and information security measures.

Comeleak
In 2016, the Commission on Elections (COMELEC) suffered a massive data breach. This exposed the personal information of millions of voters.
The initial hacking of the website of the Commission on Elections was on March 27, 2016, by a group identifying itself as Anonymous Philippines. The homepage was defaced with a message accusing COMELEC of not doing enough to ensure the security of voting machines used in the country’s upcoming election.
The breach was later called “Comeleak” after the hackers obtained the personal information of over 55 million registered voters, including names, birthdays, home and email addresses, and parents’ full names.
The Enigma of the Cebuana Marketing Server Breach and its Link to the DFA
In 2019, Cebuana Lhuillier, a pawnshop and remittance company in the Philippines, admitted to the breach of one of its email servers in use for marketing purposes. This compromised the data of about 900,000 of their clients. The breach exposed personal information such as birthdays, addresses, and sources of income, but not transaction details or information.
The company assured its clients that the transaction details remained safe and secured. Moreover, the company’s main servers were not affected by the breach. The breach involved an email server used for marketing. Although attempts to infiltrate one of its servers were detected on January 15, unauthorized downloads went back to August 2018.
The company immediately disconnected the server from the network after confirmation of the breach. They also reported the incident to the National Privacy Commission.
Wendy’s and Jollibee Called to Action on Data Breach Prevention
In May 2018, the National Privacy Commission (NPC) of the Philippines ordered fast-food chains Wendy’s and Jollibee to take preventive measures against data breaches. Here are some more details about the case:
- Wendy’s PH website was hacked, exposing thousands of personal data of the fast-food chain’s customers and job applicants.
- The direct order on Jollibee Foods Corporation (JFC) was to suspend its online delivery system over vulnerabilities on its website.
- The data of 18 million people in the online delivery database of JFC were in “high risk” of exposure to harm due to vulnerabilities in the system, although there were no breaches yet to the database.
- The NPC ordered Jollibee to suspend operations of its online delivery system until the resolution of the site’s vulnerabilities.
- The NPC also ordered Jollibee to “employ privacy by design” in re-engineering JFC Group’s data infrastructure.
- The NPC gave Jollibee 10 days to come up with a plan to rehabilitate the vulnerabilities on its website.
- The NPC also ordered Wendy’s Philippines to promptly notify data subjects affected in the breach and wholesale leak of its database.
BDO Unibank Inc. Under Scrutiny by NPC for Alleged Data Breach in 2021
In December 2021, the National Privacy Commission (NPC) announced the possible data breach of BDO Unibank Inc. The breach involved the possible compromise of multiple BDO accounts. The NPC urged the bank to take immediate action to address the issue. The breach came to light after more than 700 customers of BDO fell victim to a heist perpetrated by an unidentified group of hackers.
The bulk of unauthorized online bank transfers from the customers’ hacked accounts were allegedly the work of a certain “Mark Nagoyo.” The National Bureau of Investigation (NBI) arrested five persons. They are believed to be behind the massive hacking incident that targeted customers of BDO Unibank in January 2022. Two of the suspects, both Nigerians, were caught in an entrapment operation in Mabalacat, Pampanga on Jan. 18. The bureau identified them as Ifesinachi Fountain Anaekwe, also known as “Daddy Champ,” and Chukwuemeka Peter Nwadi.
The Monetary Board ordered sanctions on BDO Unibank Inc. and Union Bank of the Philippines (UnionBank) over incidents of hacked accounts in April 2022. The action ensures that both banks will swiftly address the issues that paved the way for unauthorized access to BDO accounts and the transfer of funds mostly to Union Bank accounts.
2023 Data Breach Scandal: PNP, NBI, BIR, and SAF Records Among the Exposed Data
In 2023, a massive data breach exposed the personal information of millions of Filipinos, including records from crucial institutions like the Philippine National Police (PNP), National Bureau of Investigation (NBI), Bureau of Internal Revenue (BIR), and Special Action Force (SAF). Here are some more details about the case:
- The breach came to light on October 3, 2023, when hackers released a massive trove of personal data from the servers of the Philippine Health Insurance Corporation (PhilHealth), after the state insurer refused to pay a ransom of US$300,000.
- The breach affected millions of people, including domestic residents and overseas Filipino workers in places such as Hong Kong.
- The hackers claimed to have hacked into the servers of the Philippine Statistics Authority. This handles the country’s national identification cards. The Philippine National Police’s forensics database which contains case files on the victims of rape, among other crimes. Also, the websites of the Department of Science and Technology, the Technical Education and Skills Development Authority (Tesda), and Clark International Airport.
- The breach exposed highly sensitive data such as fingerprint scans, birth certificates, tax identification numbers (TIN), tax filing records, academic transcripts, and even passport copies.

Final Thoughts
Employees are often the first line of defense in data security. Regular training and education on data privacy and information security are vital to ensure that they understand the importance of these concepts and their roles in protecting sensitive information.
ECCI offers tailored solutions, including assessments, policy development, training, and incident response, to bolster data privacy and information security. Our experts can also ensure regulatory compliance. Need tailored solutions? Contact us today for a conversation on how we can customize strategies to suit your unique needs and goals. Your journey toward lasting success begins here.
In conclusion, data privacy and information security are inextricably linked. They are working together to protect sensitive data in our digitally driven world. By understanding their co-relation, adhering to best practices, and learning from real-world cases, organizations can build a robust defense against data breaches and uphold the principles of confidentiality, integrity, and availability. The stakes are high and the responsibility is greater. However, with a comprehensive strategy, businesses can confidently navigate the complex landscape of data privacy and information security.









One Response
Hi Team,
I understand that your inbox is likely inundated with messages from outreach experts vying for your attention. It’s a daunting race, and yet here I am, hoping to make a meaningful connection.
I’m Georgia, and I specialize in Link Insertion expertise. I know, it’s tempting to overlook yet another outreach attempt, but I promise, this one might just catch your eye.
In the various niches, we’ve had the privilege of working with numerous sites, crafting safe and competitive backlink profiles at remarkably competitive rates.
Here’s what sets us apart:
1. Backlinks from sites boasting a DR30+ and 1000+ traffic, validated by the almighty Ahrefs.
2. You’ll have the opportunity to review all prospects before your links are published.
3. None of these sites/links will contain undesirable phrases like ‘write for us’ or ‘free guest post’.
Our team, based in Chiang Mai, Thailand – the SEO capital of the world and the Digital Nomad hub of Asia, is committed to delivering results that exceed expectations.
I understand if you’re hesitant to explore new opportunities, but I assure you, this one is worth your consideration.
Would you be open to learning more about our process and how it can elevate your backlink strategy?
Cheers,
Georgia Anderson
Outreach Manager
TBP Agency
C/o Yashaswani